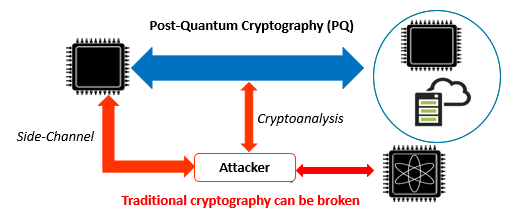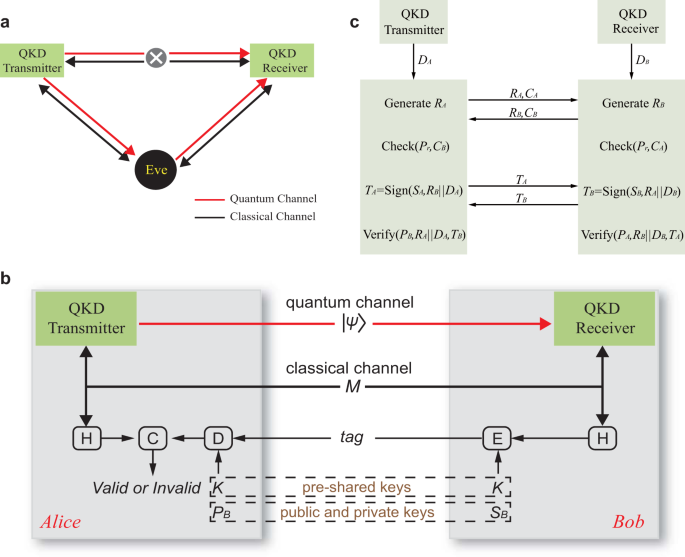
Experimental authentication of quantum key distribution with post-quantum cryptography | npj Quantum Information
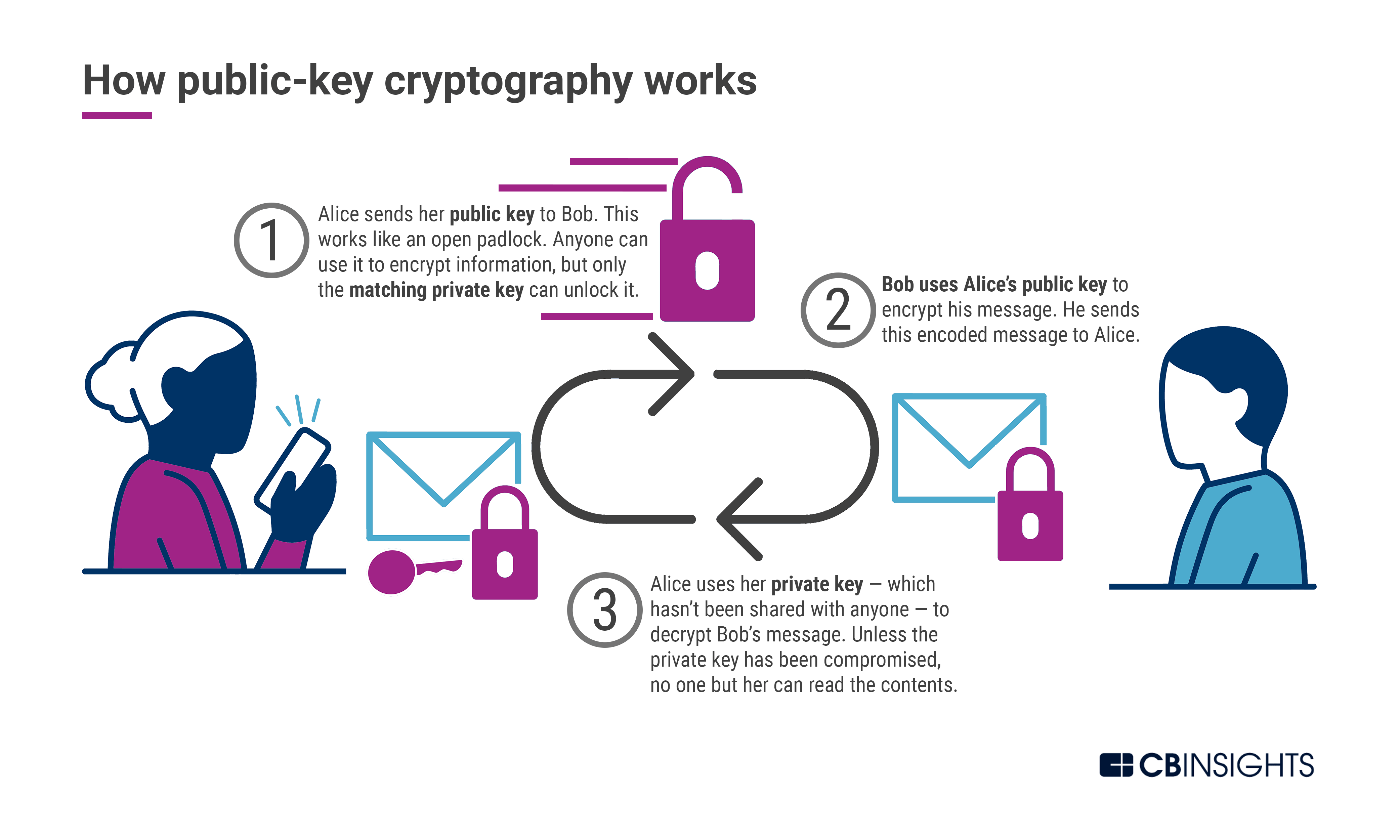
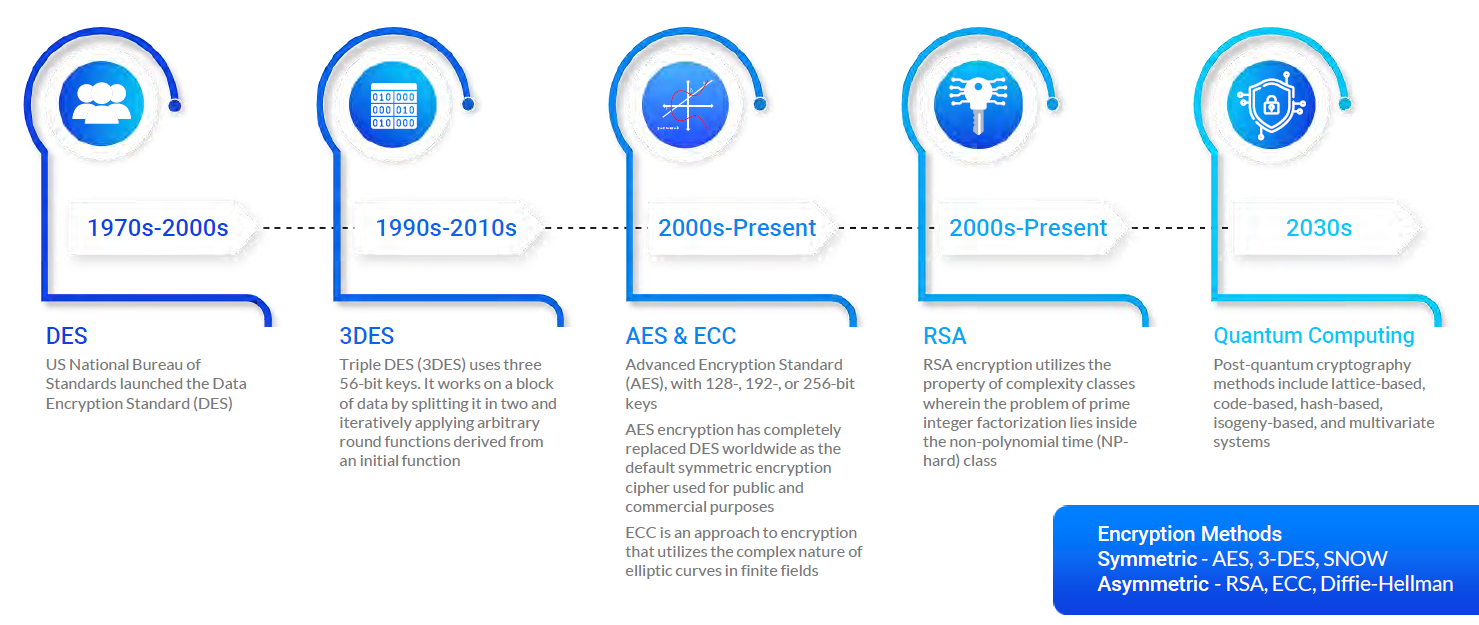
Post-Quantum Cryptography: A Look At How To Withstand Quantum Computer Cyber Attacks - CB Insights Research

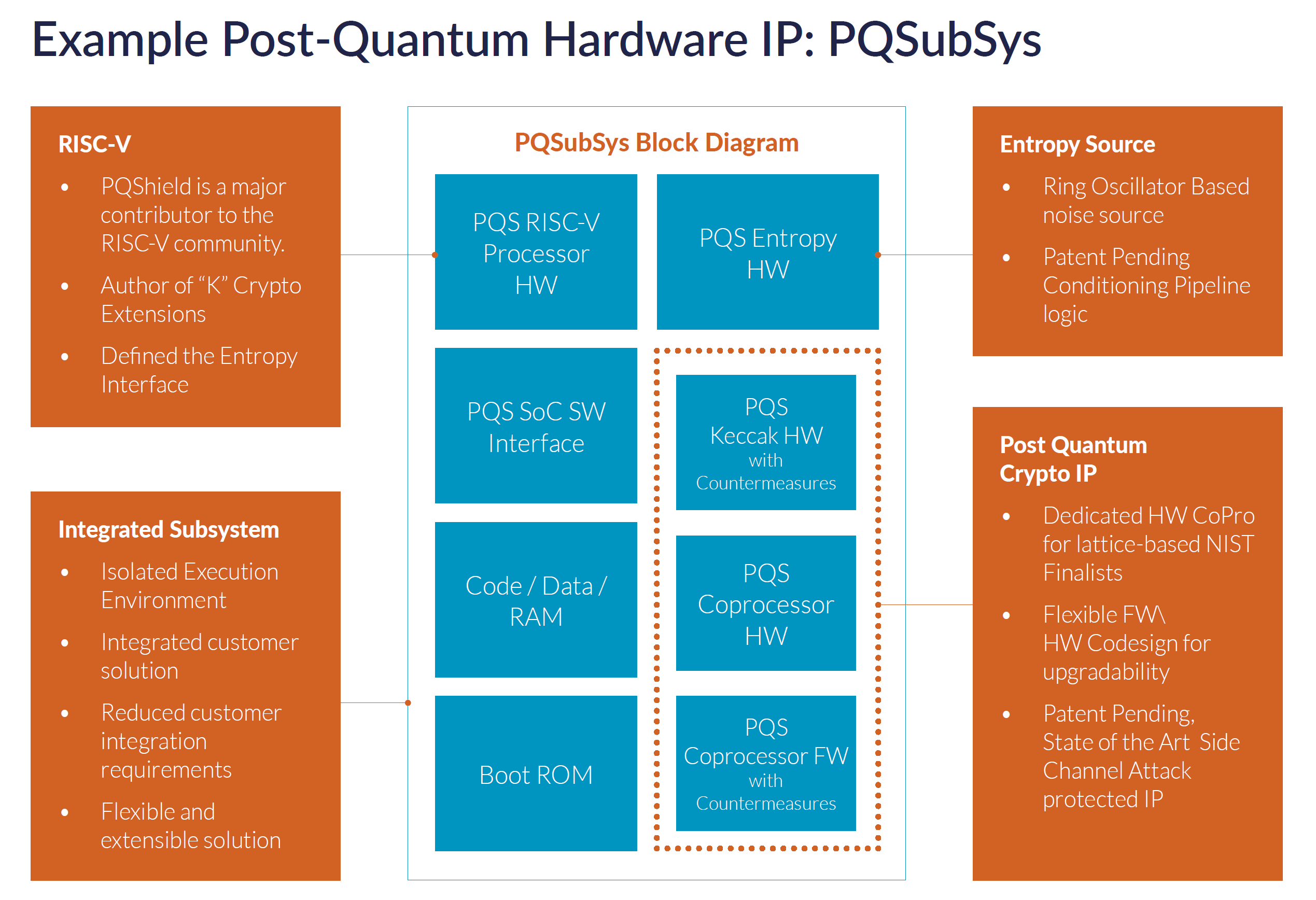
Emerging Post Quantum Cryptography and the Importance of PUF based Root of Trust - Global Semiconductor Alliance

Evaluation of Post-Quantum Distributed Ledger Cryptography | Published in The Journal of The British Blockchain Association
Post-Quantum Cryptography: A Look At How To Withstand Quantum Computer Cyber Attacks - CB Insights Research