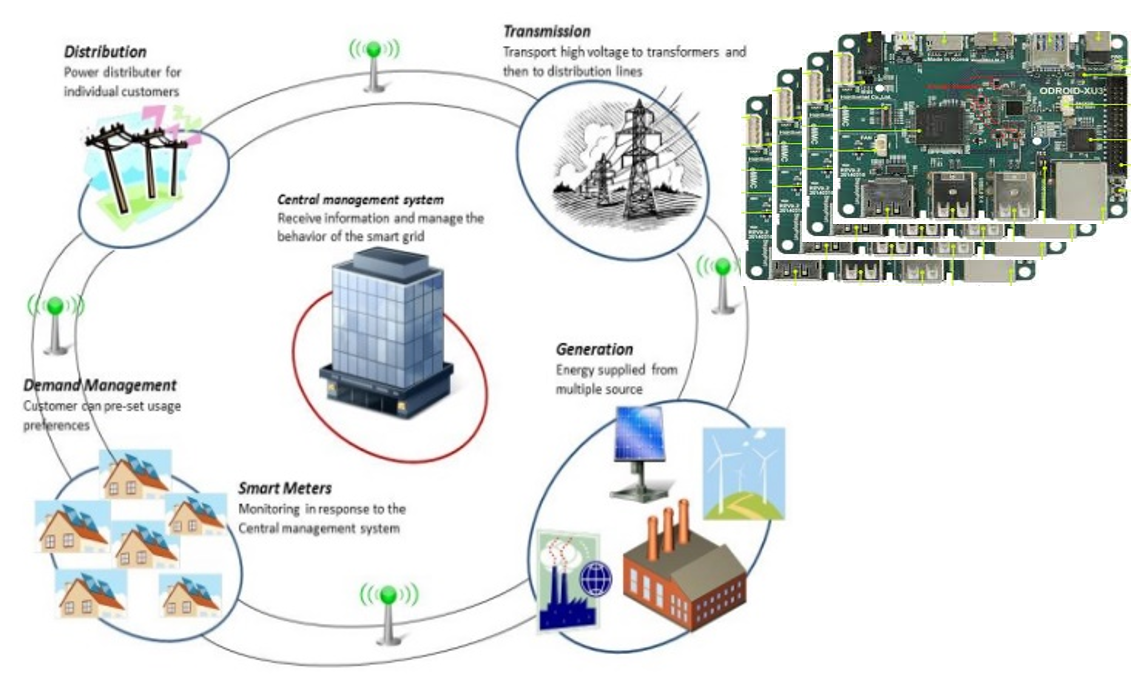
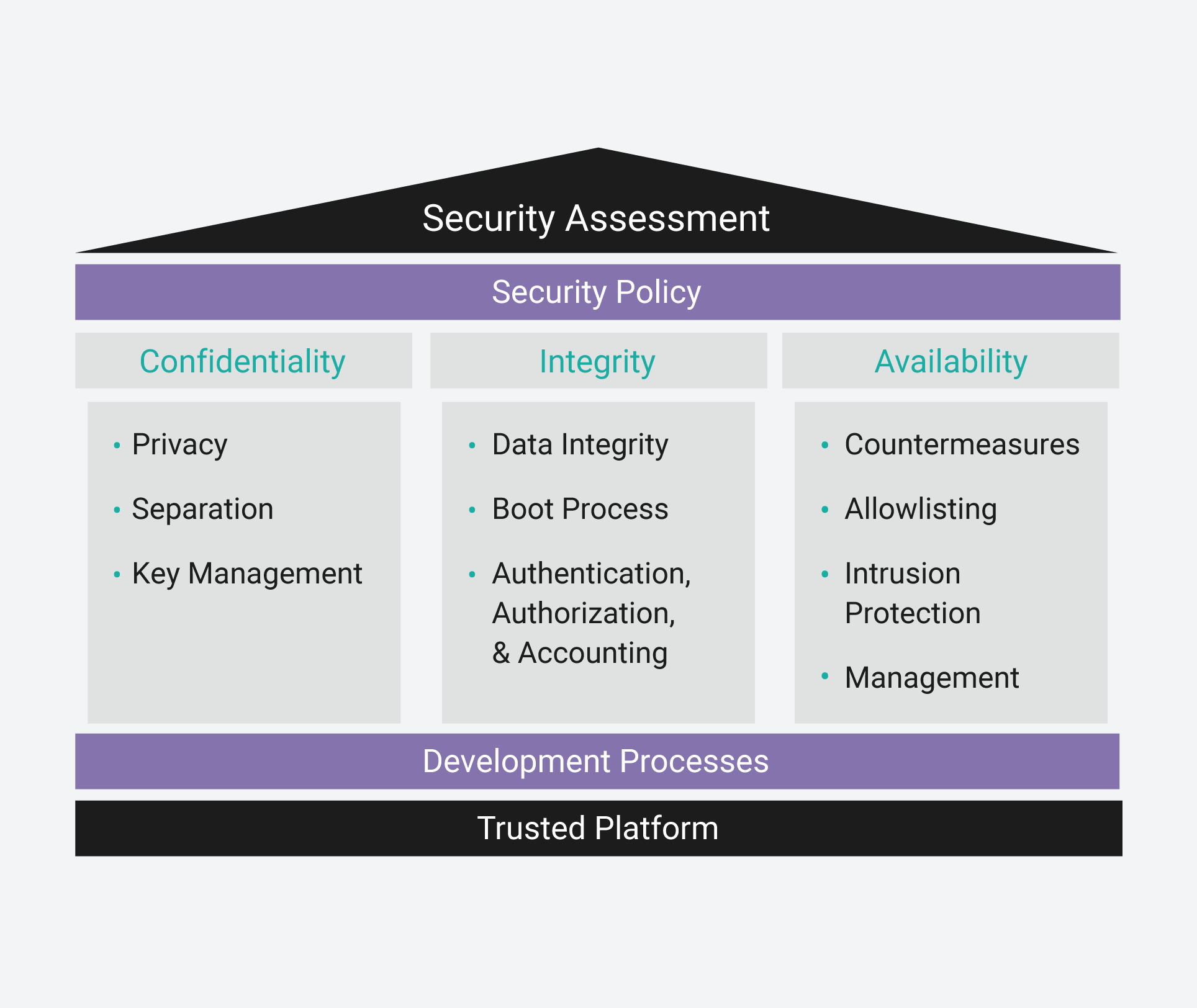
Amazon.fr - Embedded Systems Security: Practical Methods for Safe and Secure Software and Systems Development - Kleidermacher, David, Kleidermacher, Mike - Livres

Secure embedded system hardware design – A flexible security and trust enhanced approach - ScienceDirect







.jpg?lang=en-US&width=700&height=697)