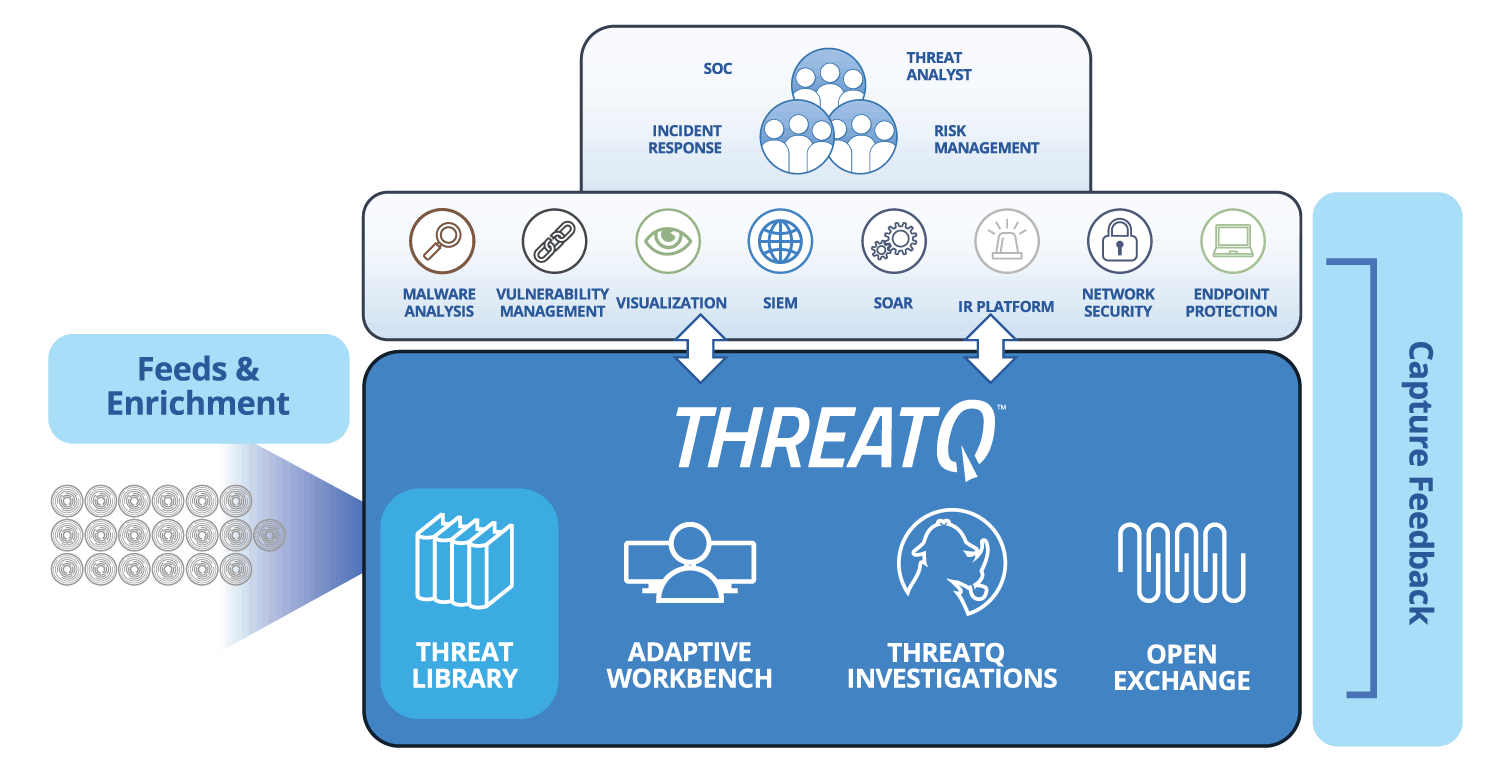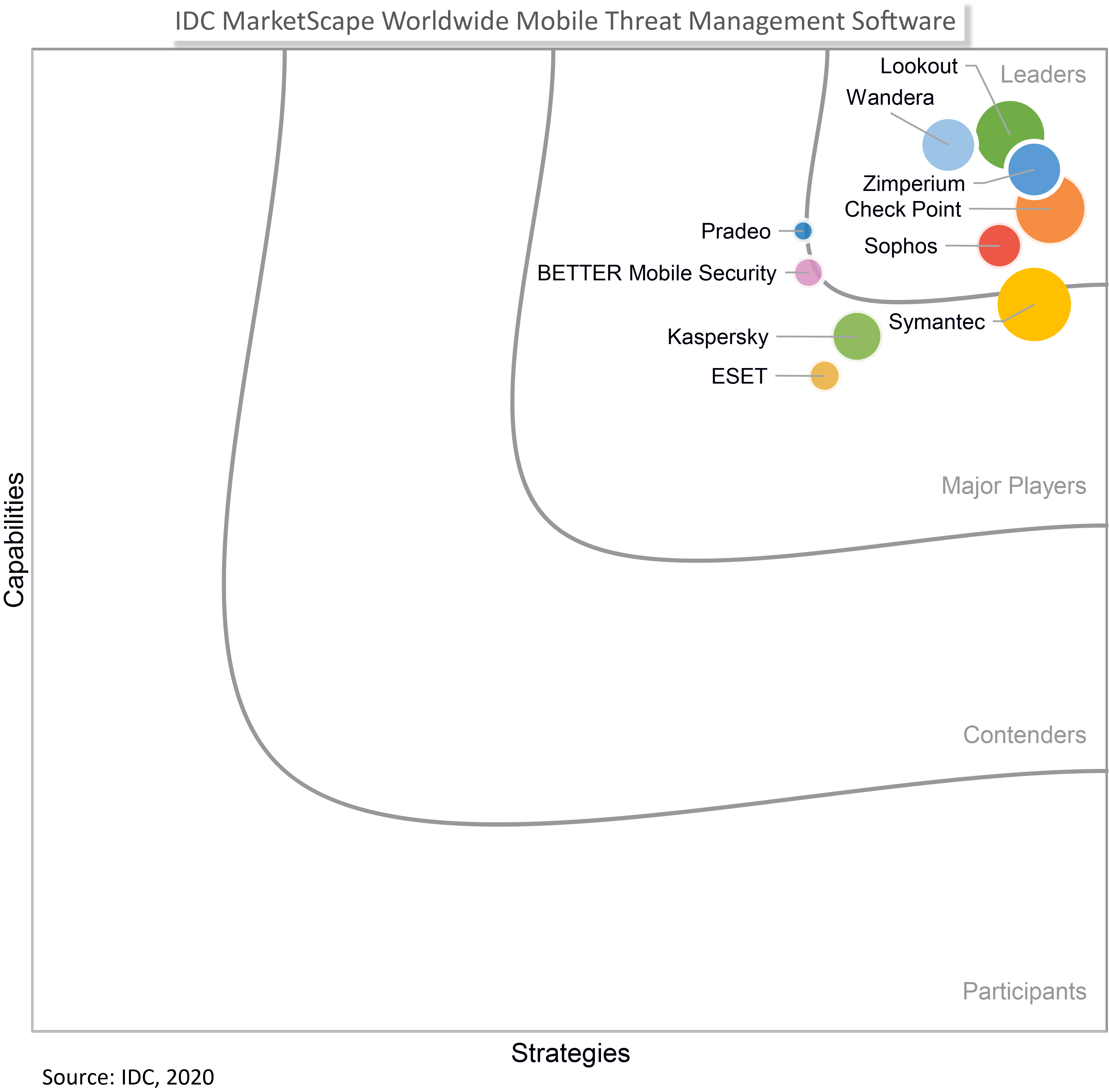
For the third consecutive time, Check Point named a Leader in the IDC MarketScape for Mobile Threat Management - Check Point Blog
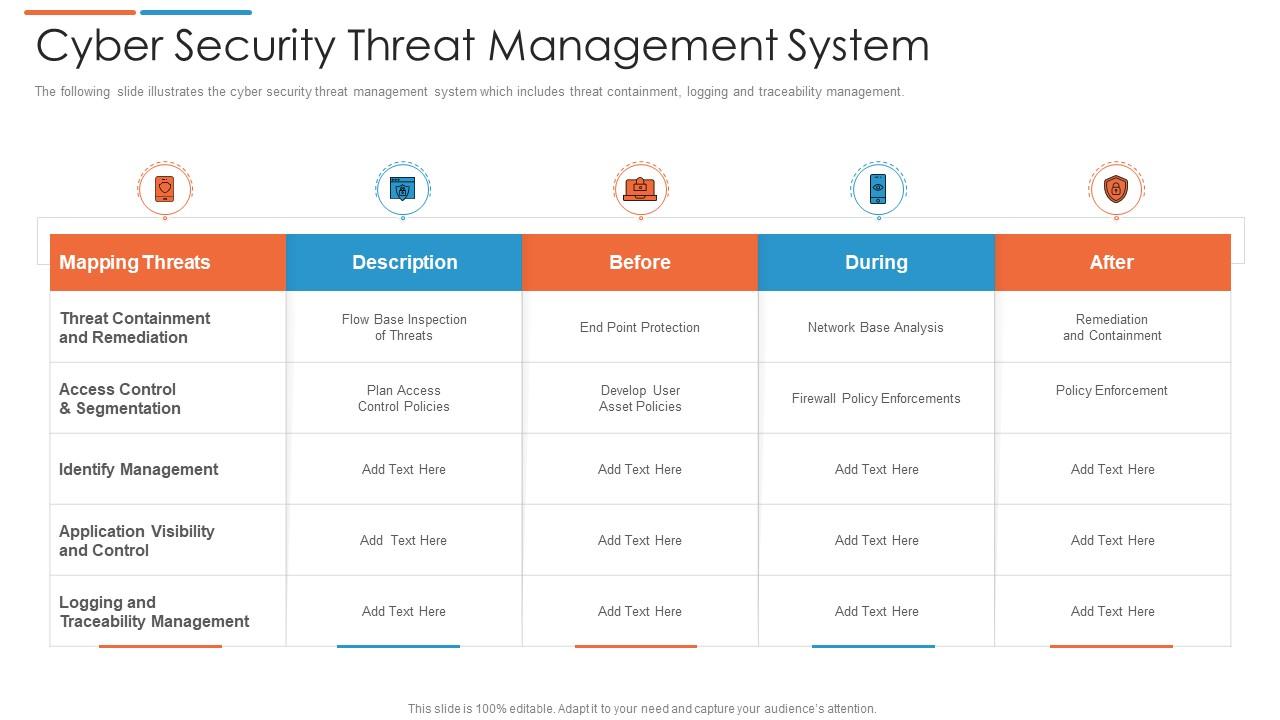
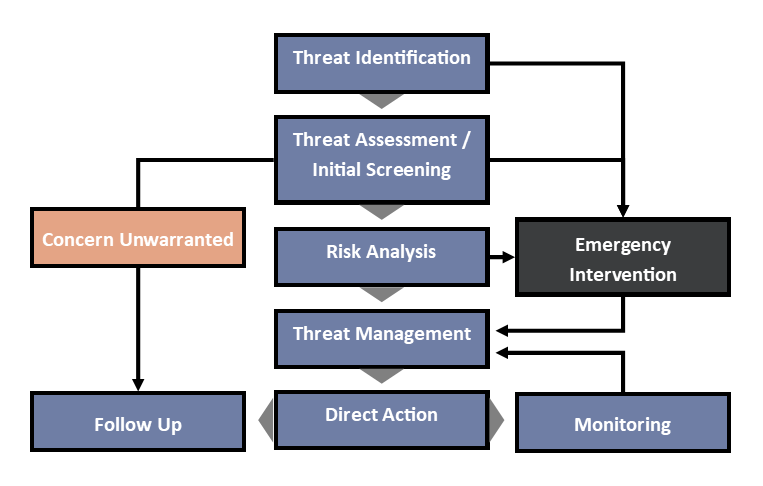
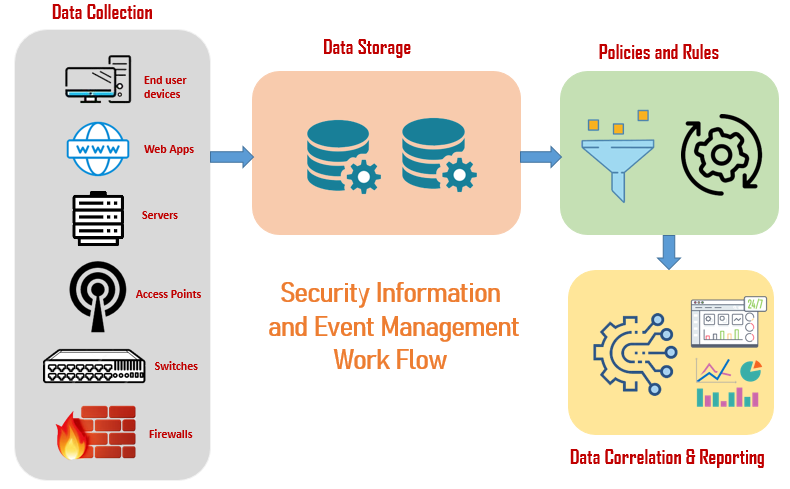
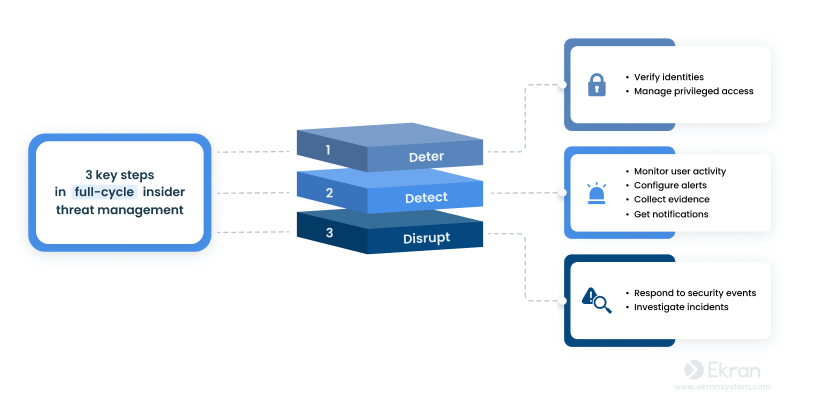
Cyber Security Threat Management System | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

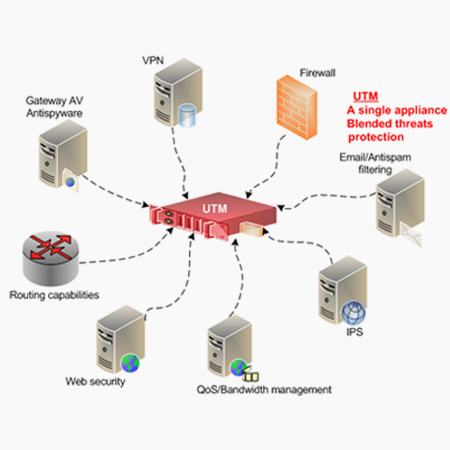
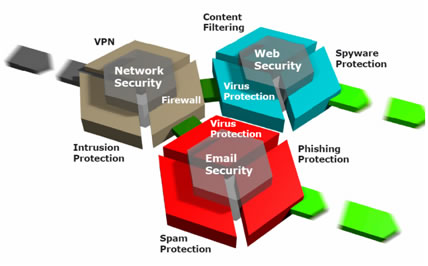
What Is Unified Threat Management (UTM)? Definition, Best Practices and Top UTM Tools for 2021 - Spiceworks

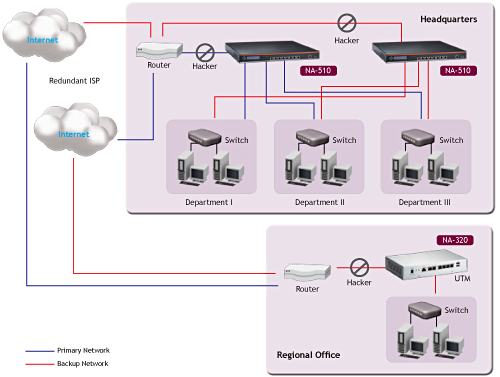
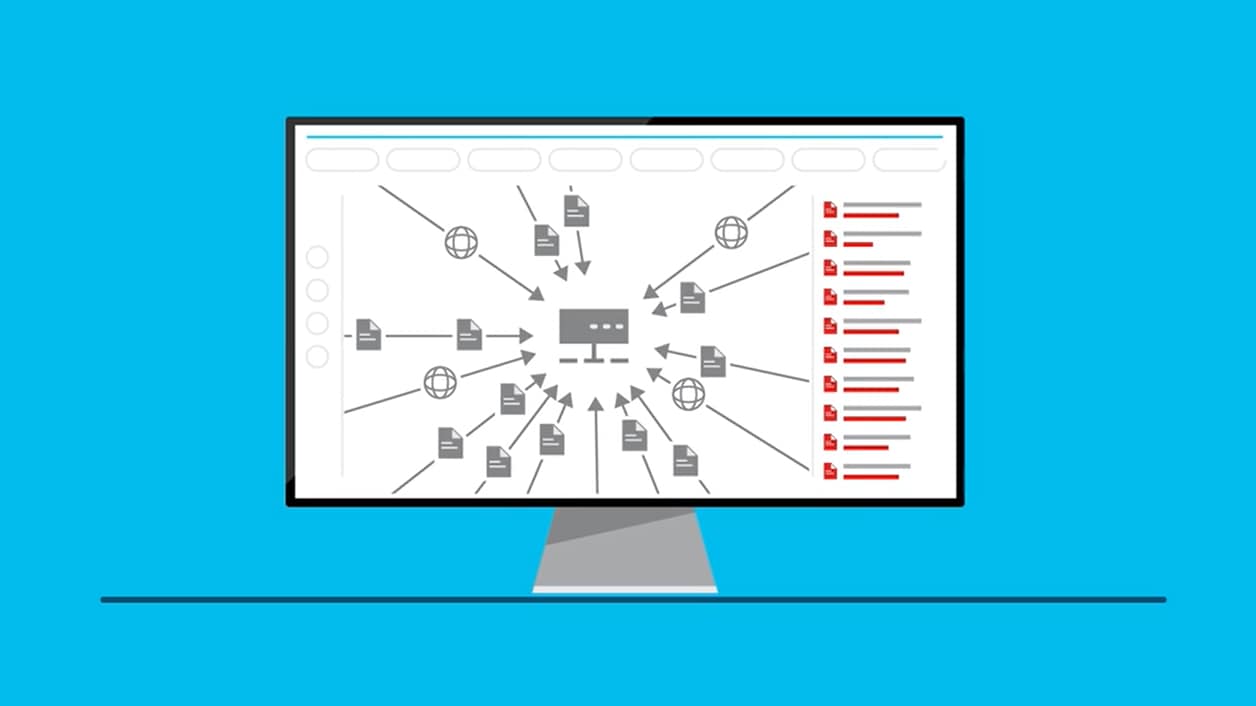
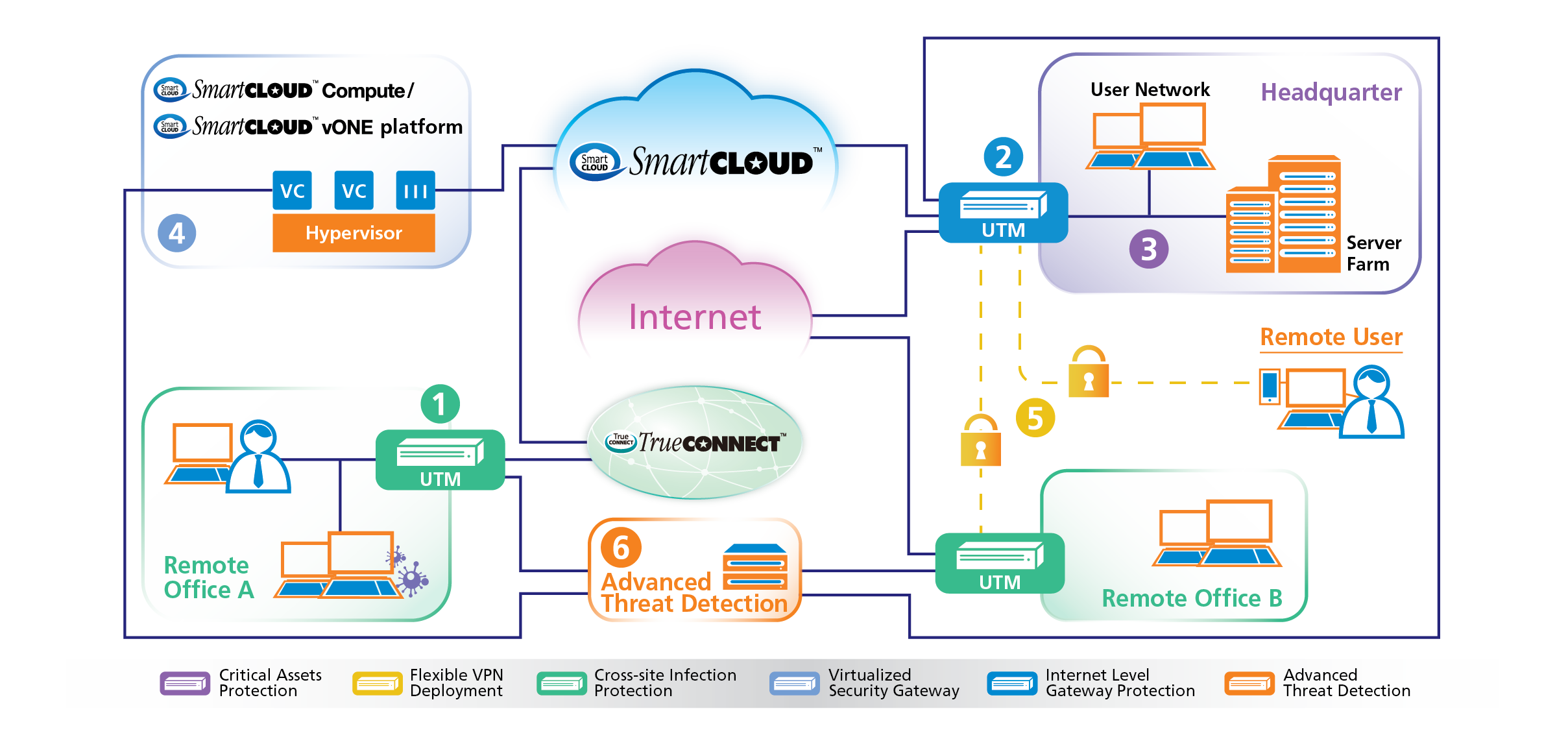
Figure 3 from Unified Threat Management System Approach for Securing SME's Network Infrastructure | Semantic Scholar

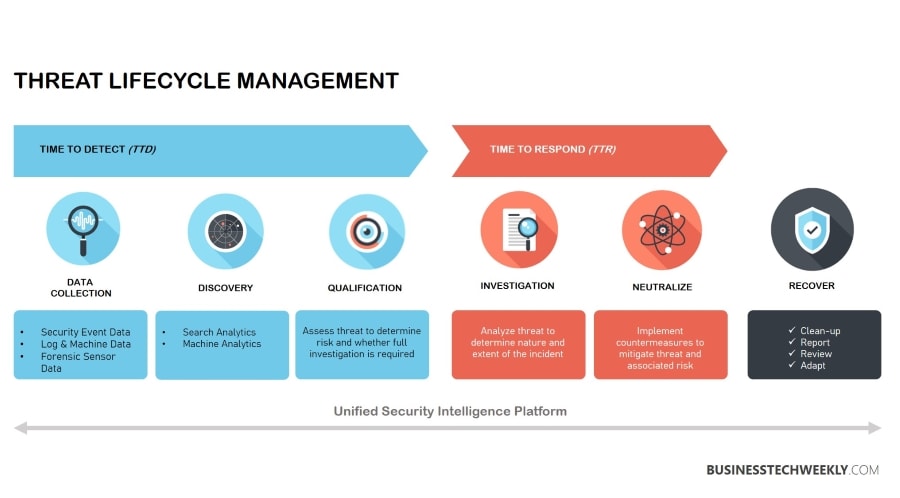
Figure 4 from Unified Threat Management System Approach for Securing SME's Network Infrastructure | Semantic Scholar