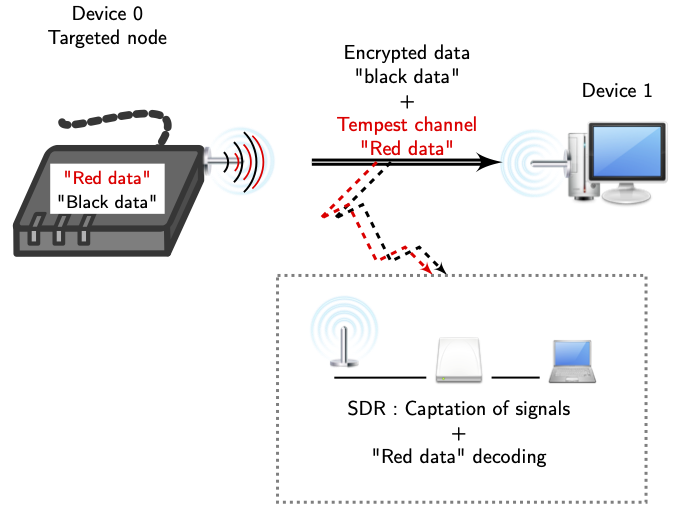
A System to Detect Sudden Epileptic Attacks Using Radio Frequency Technology | Project Ideas for BME - YouTube

U.S. review finds directed radio frequency attack likely culprit in diplomats' illnesses in Cuba | National Post

Radio Frequency Operations and Training From a Virtually Different Point of View - United States Cybersecurity Magazine

Radio Frequency: An Airbone Threat to Corporate and Government Networks | 2020-07-06 | Security Magazine
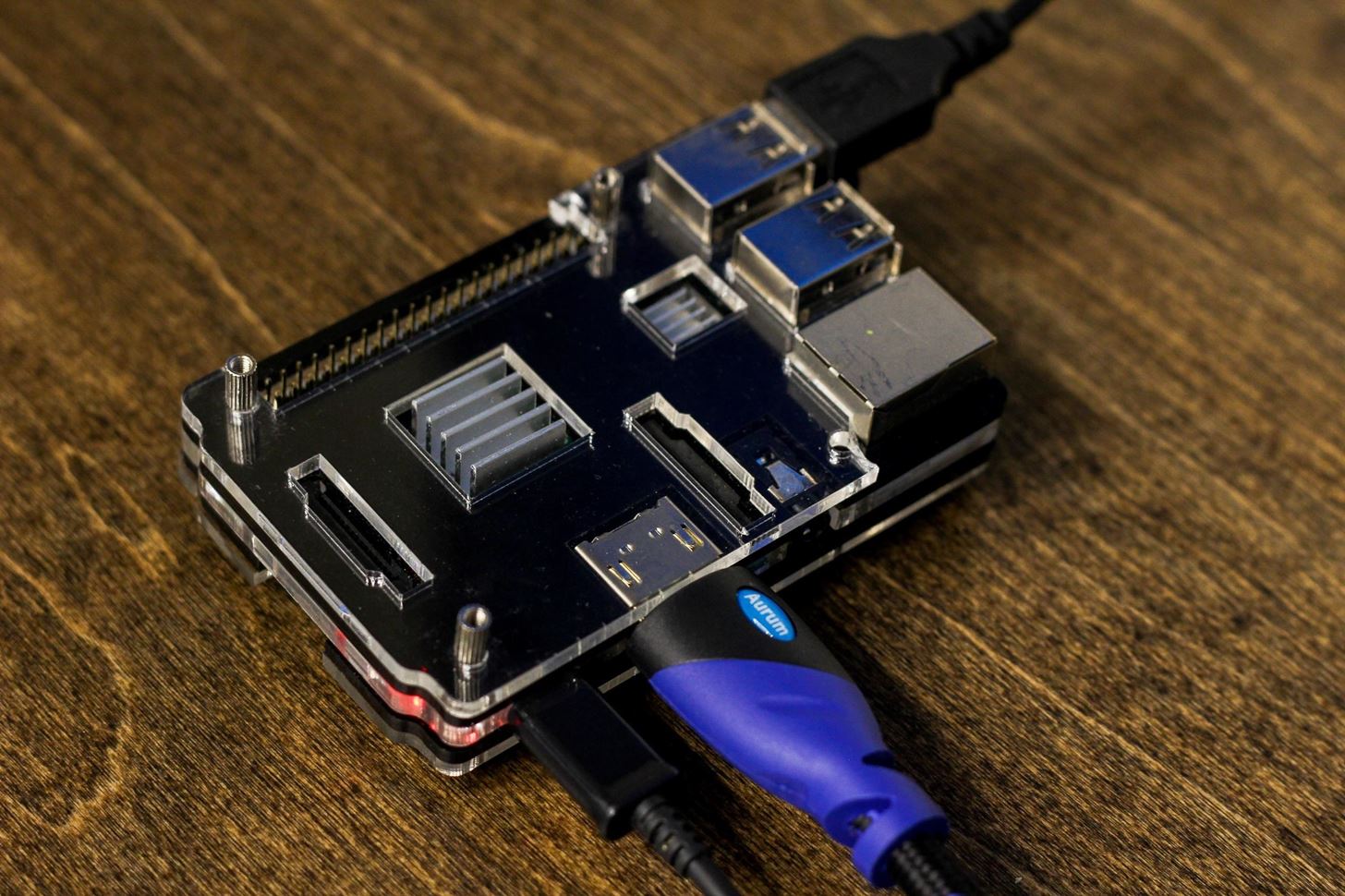
How to Hack Radio Frequencies: Hijacking FM Radio with a Raspberry Pi & Wire « Null Byte :: WonderHowTo
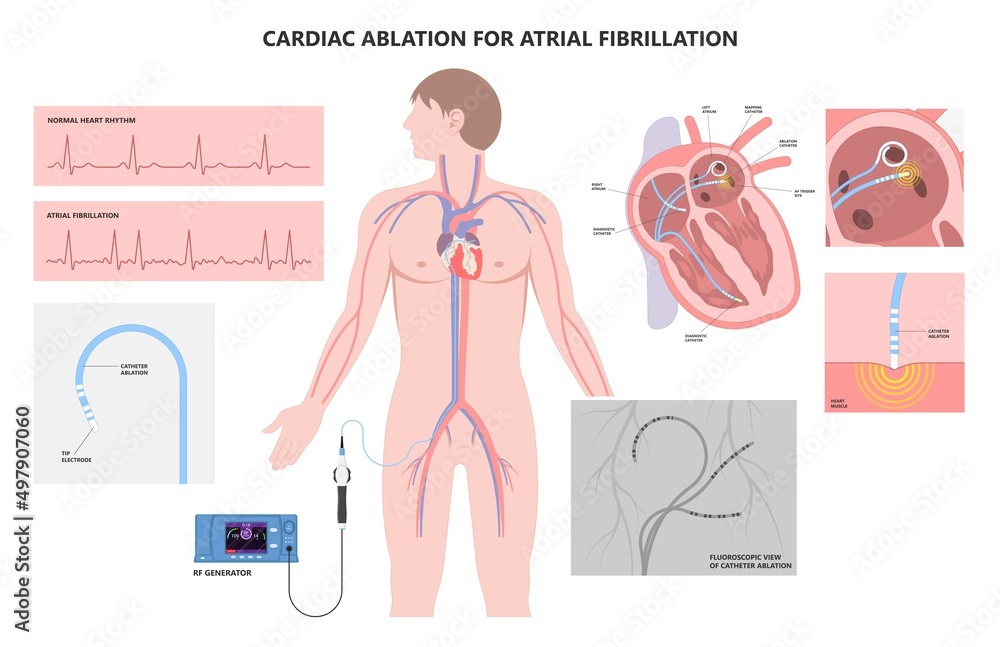
Vecteur Stock Cardiac catheter ablation treatment Atrial fibrillation rhythm problem minimally invasive procedure attack cath lab treat Coronary x-ray Radio frequency Sinus Ventricular SVT ECG ICD Radiofrequency AV | Adobe Stock

Attacks Against Industrial Machines via Vulnerable Radio Remote Controllers: Security Analysis and Recommendations - Security News
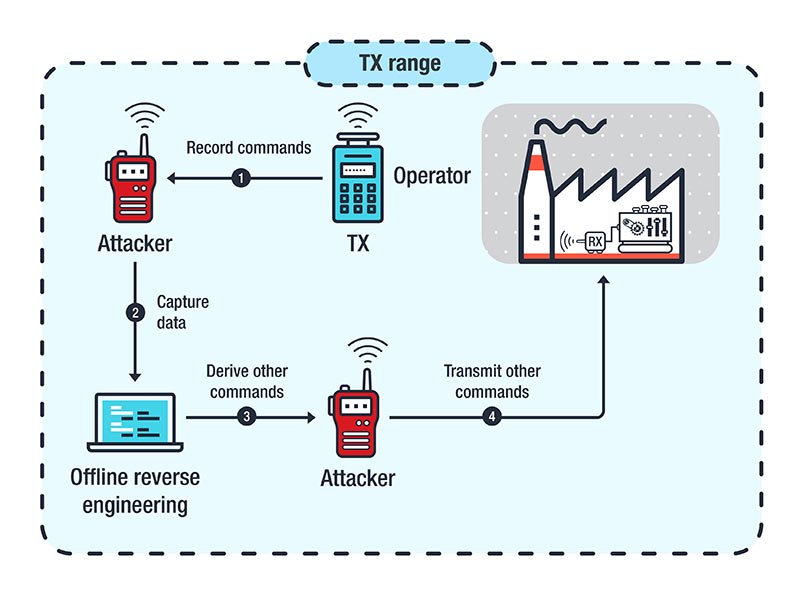
Attacks Against Industrial Machines via Vulnerable Radio Remote Controllers: Security Analysis and Recommendations - Security News





_637280703542341277.png)