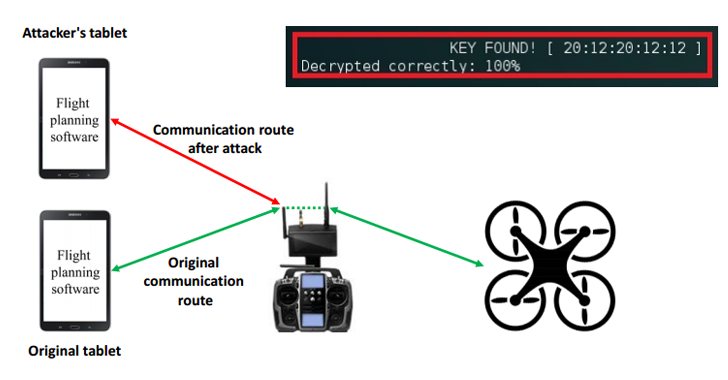
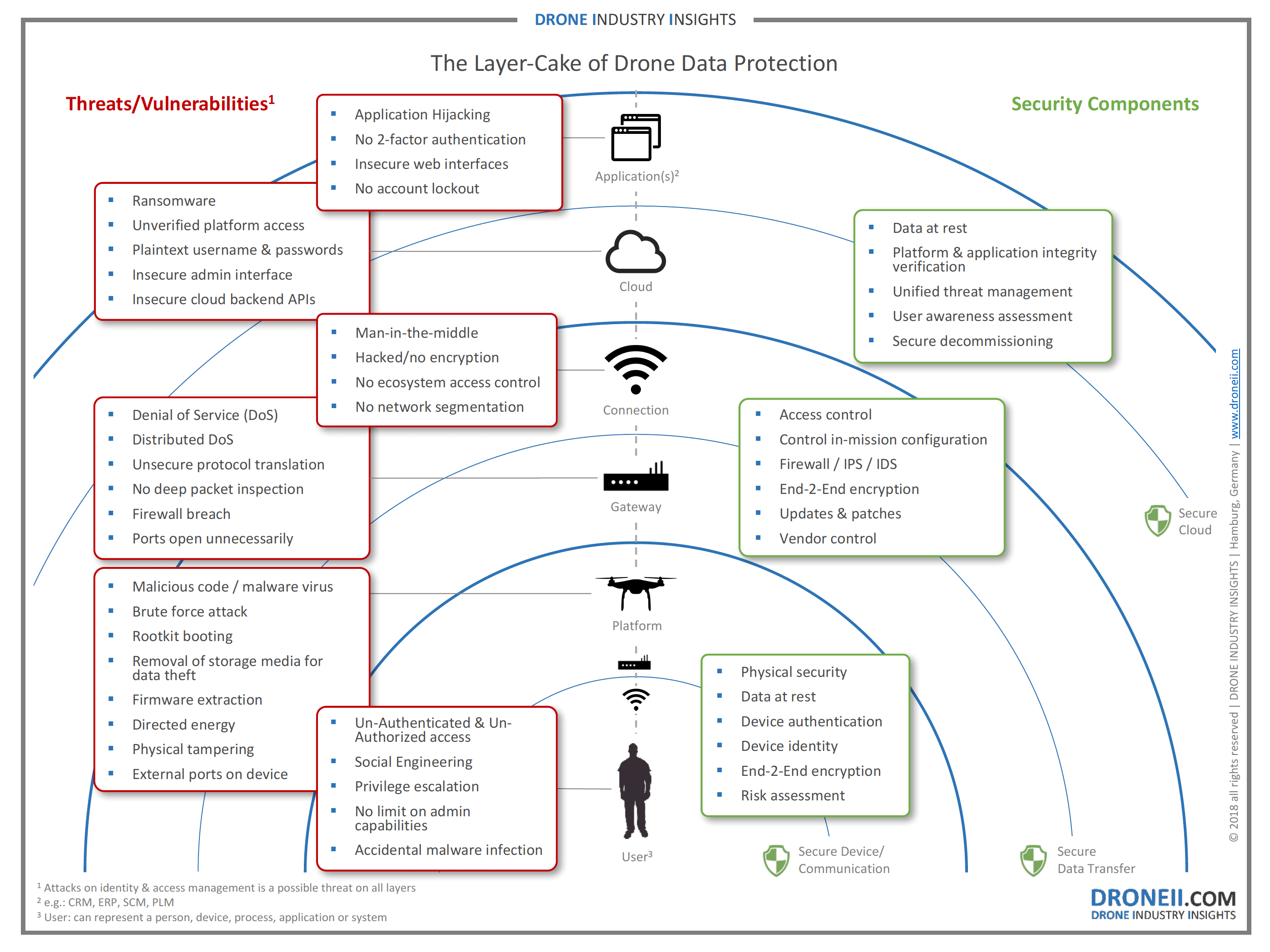
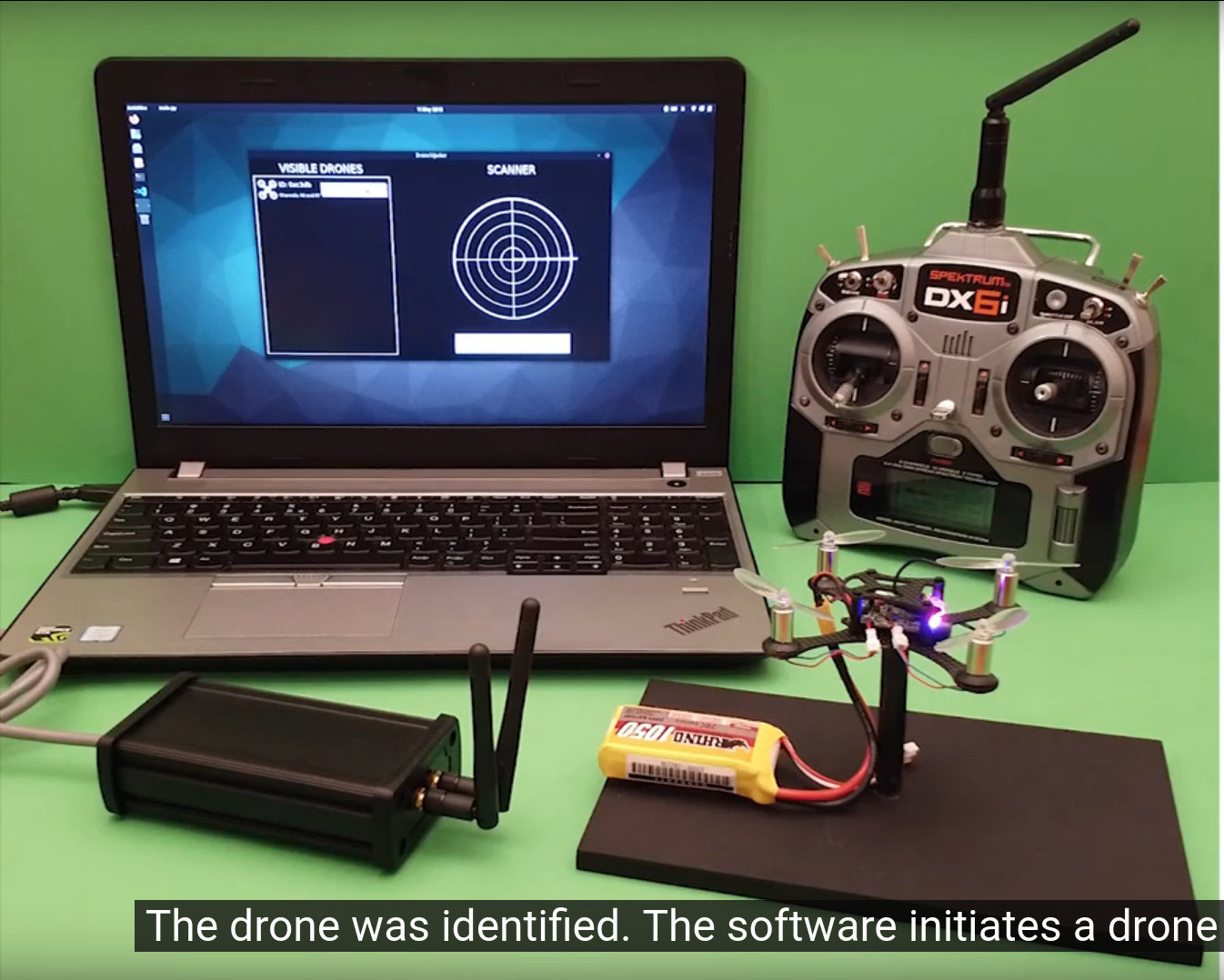
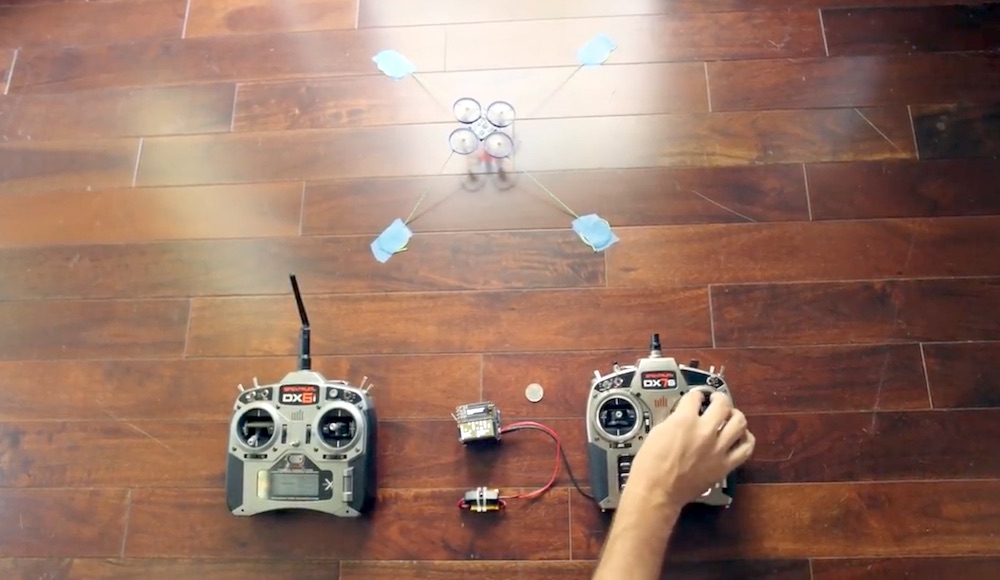
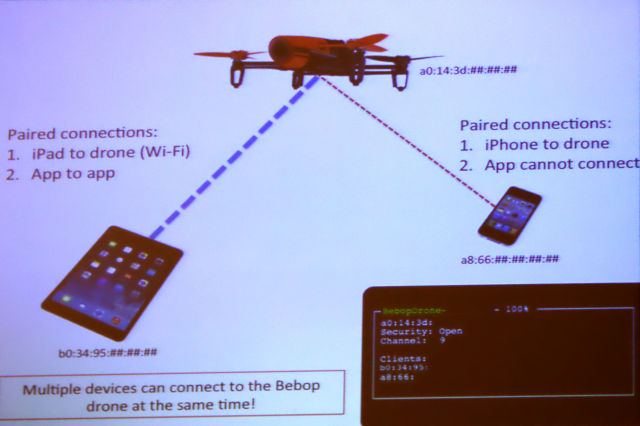
How Can Drones Be Hacked? The updated list of vulnerable drones & attack tools | by Sander Walters | Medium
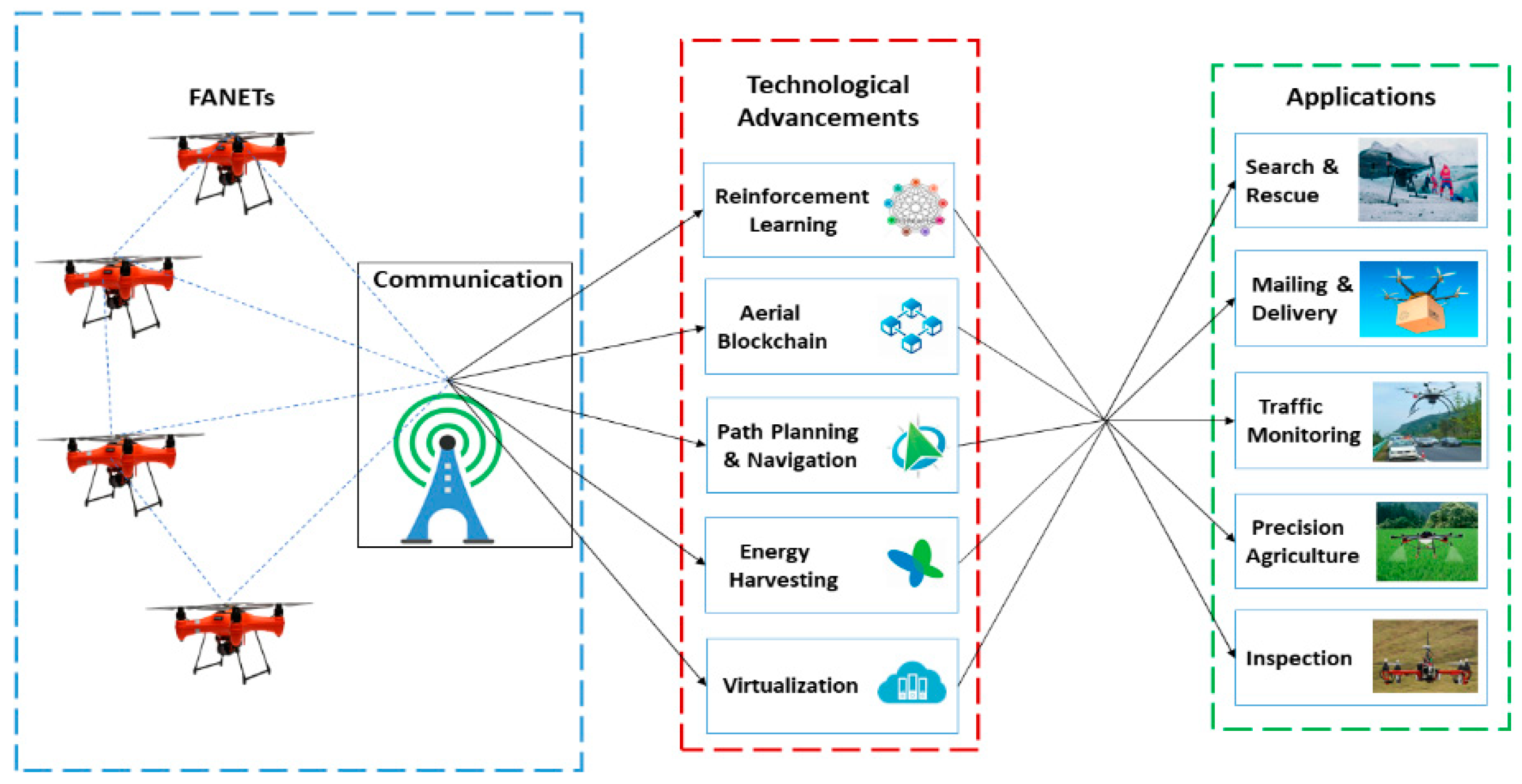
Drones | Free Full-Text | A Review on Communications Perspective of Flying Ad-Hoc Networks: Key Enabling Wireless Technologies, Applications, Challenges and Open Research Topics
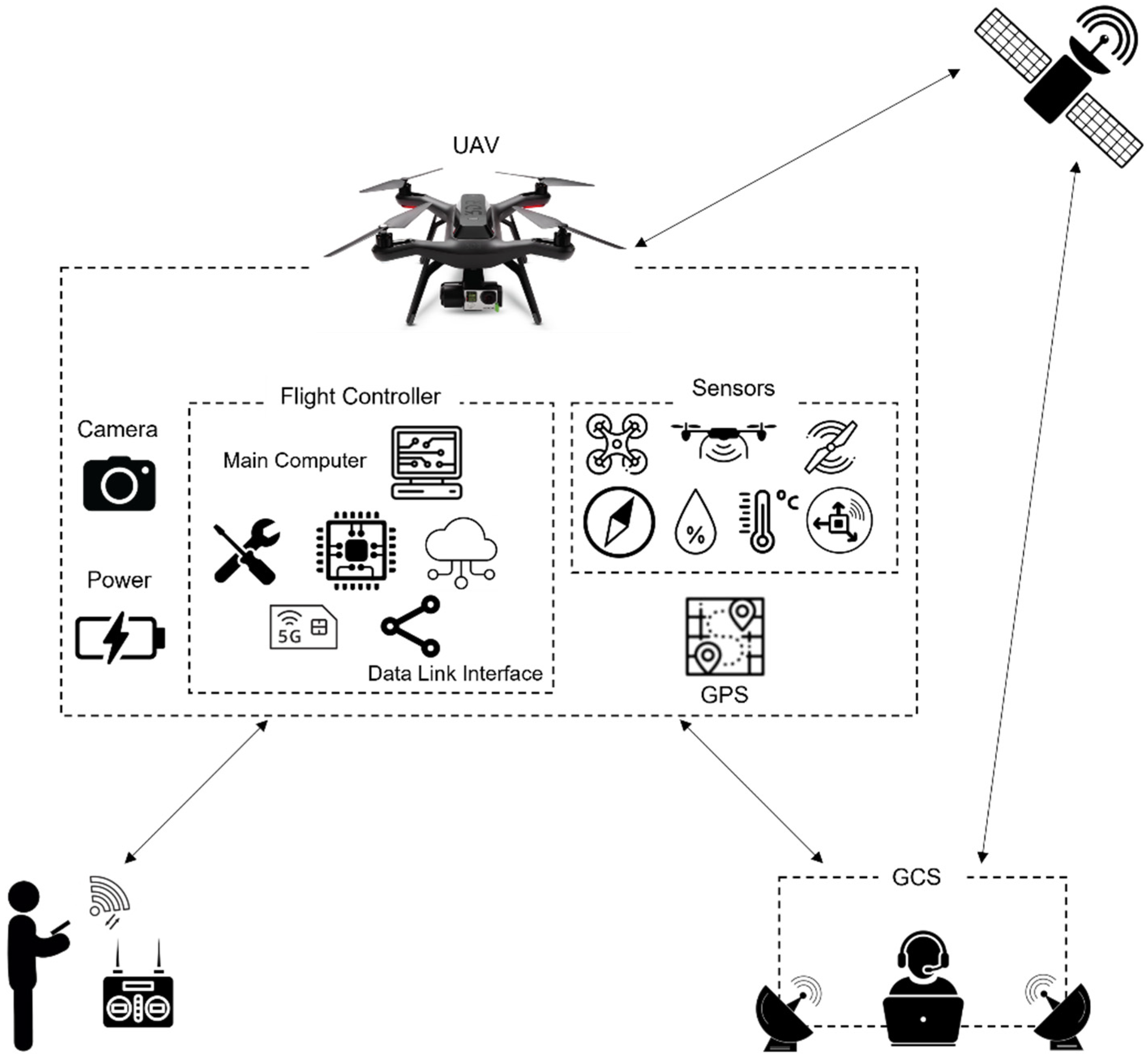
Applied Sciences | Free Full-Text | Drone and Controller Detection and Localization: Trends and Challenges

Drone Hacking and Cyber Warfare: Understanding the Potential Threats to National Security | by 0xSRF | Medium