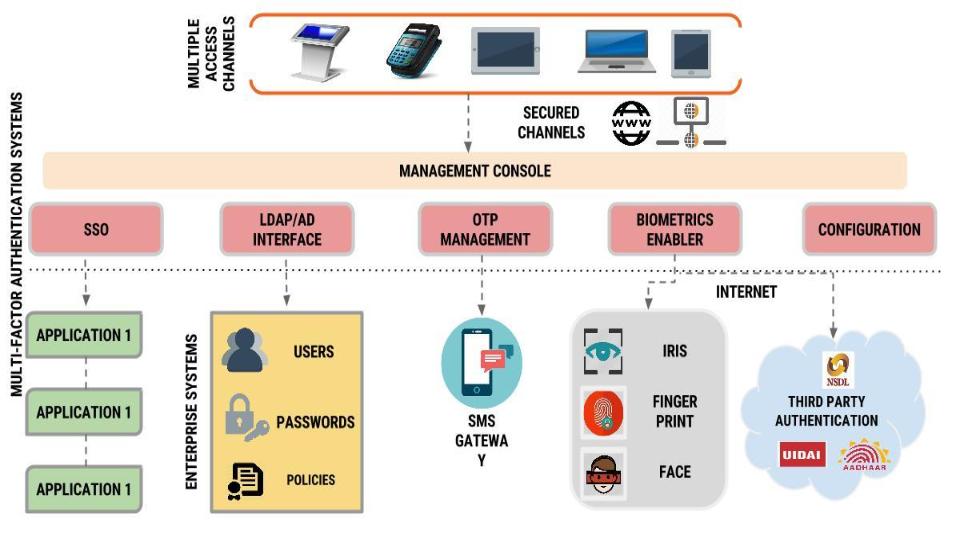
Unlocking the Secrets of Django's Authentication System: An Extensive Exploration | by elijah samson | AWS Tip
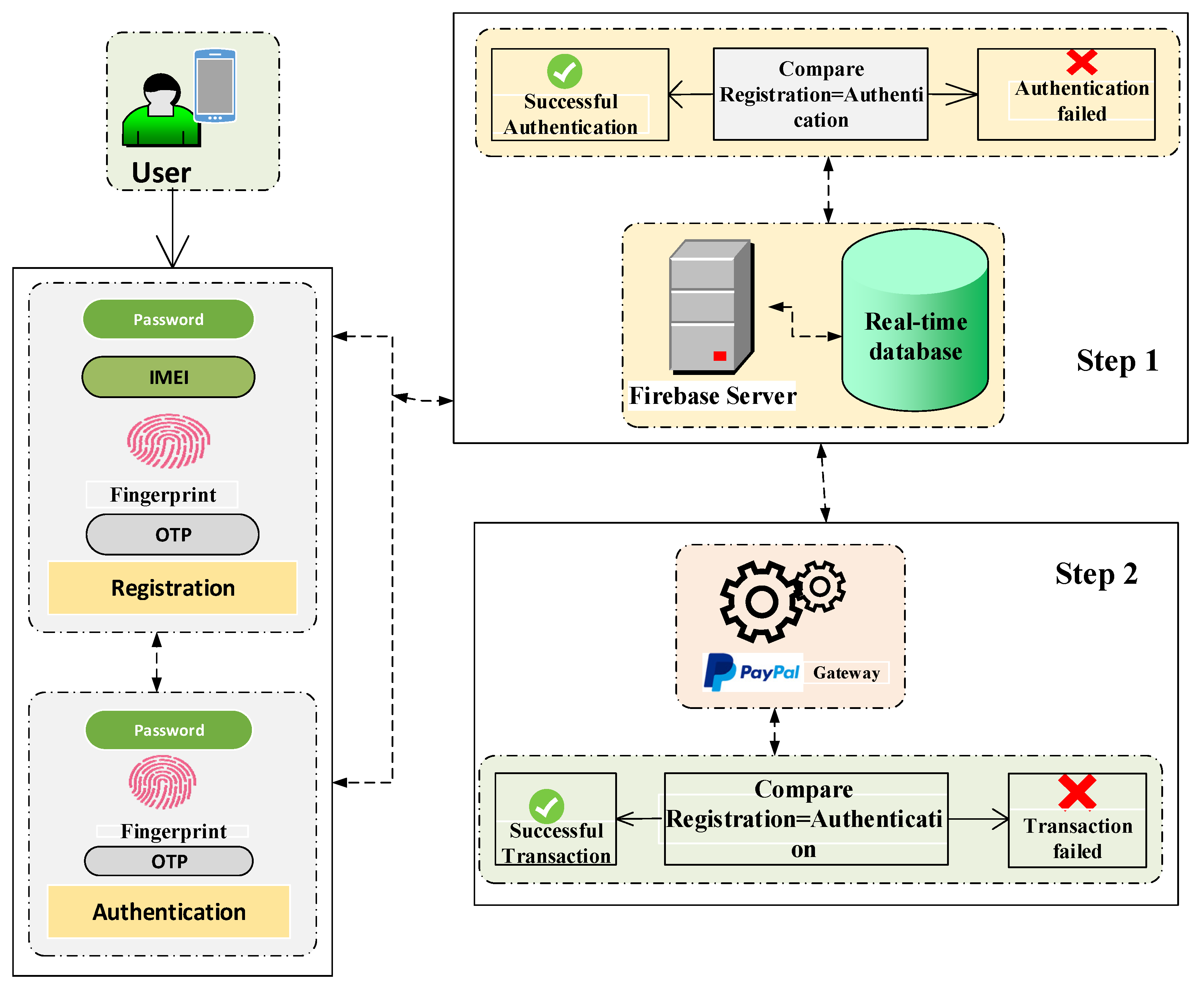
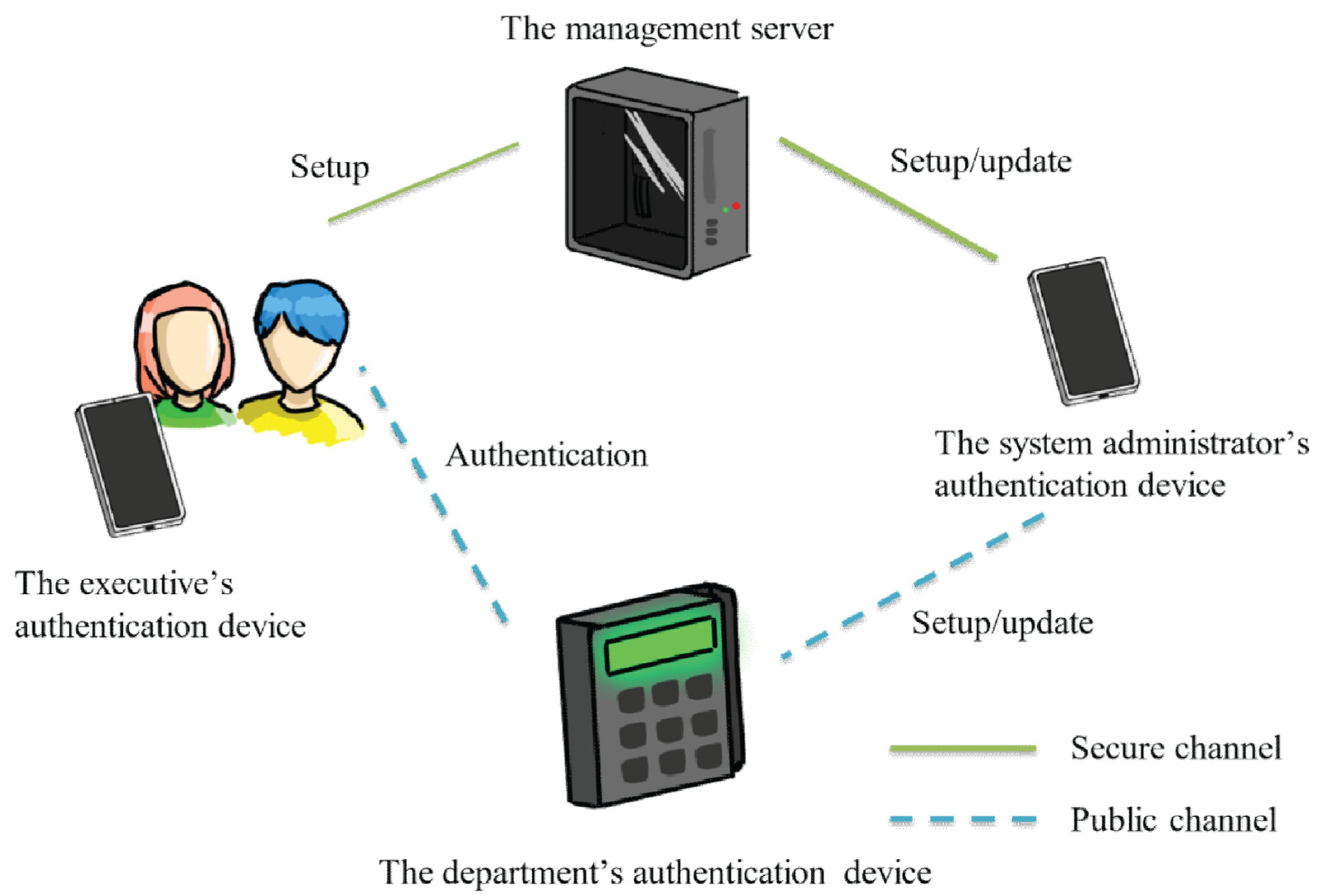
Electronics | Free Full-Text | Device Identity-Based User Authentication on Electronic Payment System for Secure E-Wallet Apps
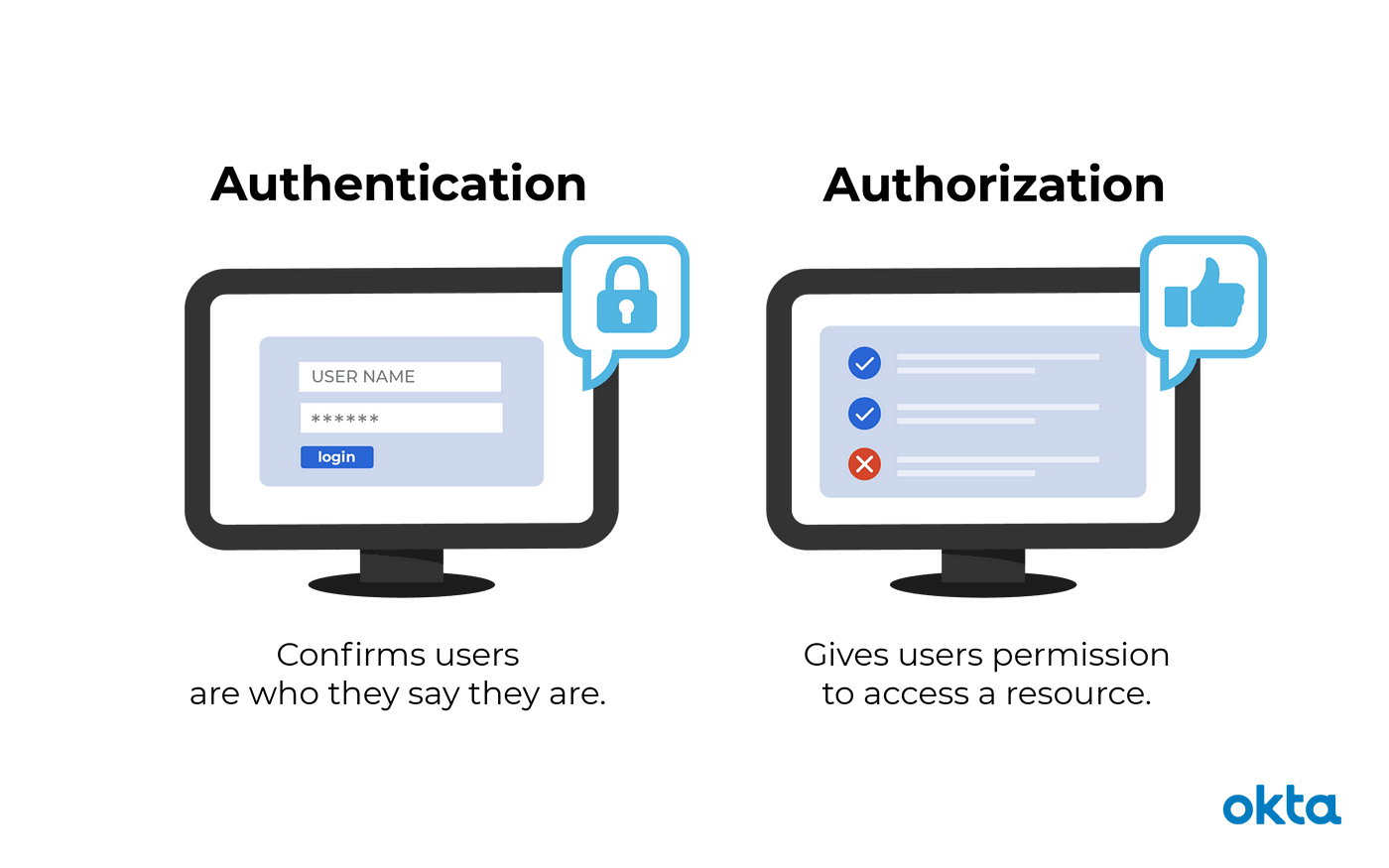
Authentication and Authorization. Visit systemdesign.us for System Design… | by PB | SystemDesign.us Blog | Medium
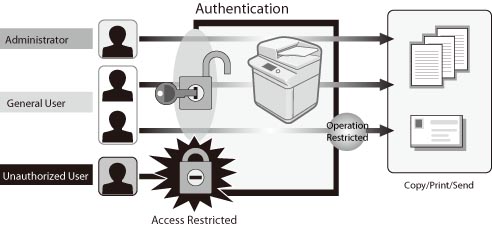
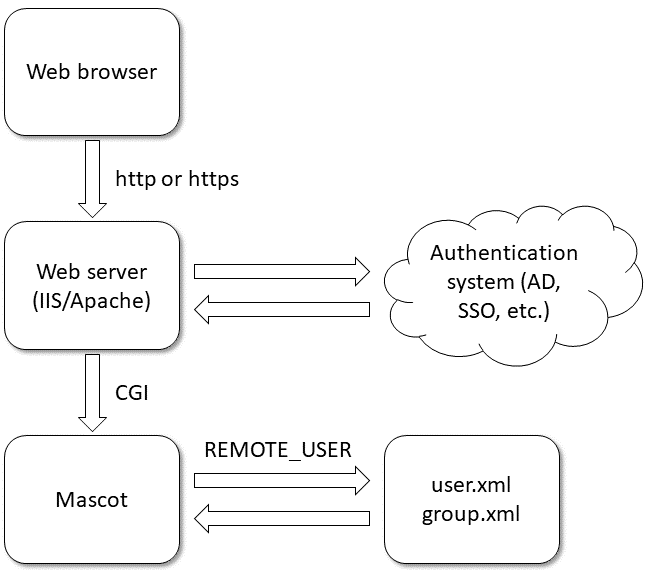
Overview of the Authentication System - Canon - imageRUNNER ADVANCE C3330i C3325i C3320 C3320i - User's Guide (Product Manual)
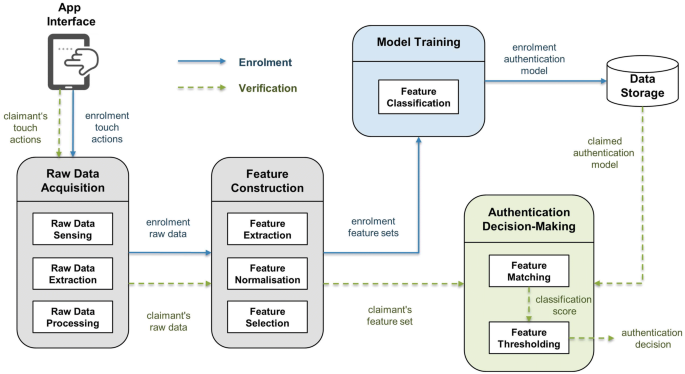
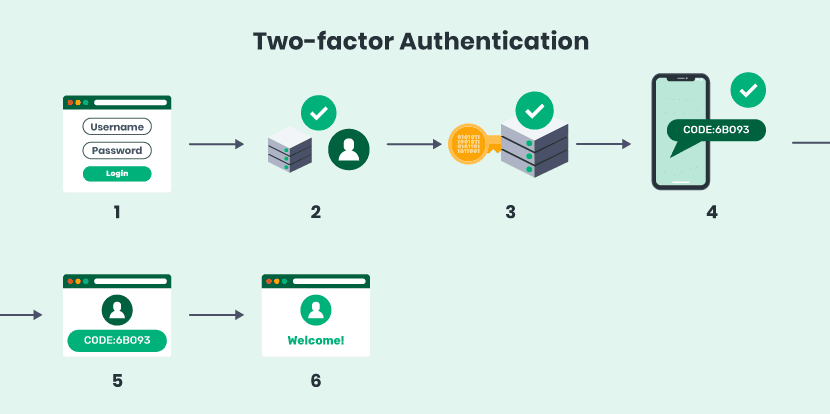




![PDF] Proposal: a design of e-learning user authentication system | Semantic Scholar PDF] Proposal: a design of e-learning user authentication system | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/62935229a5b3666237f963ba8656048c35c7a090/2-Figure1-1.png)



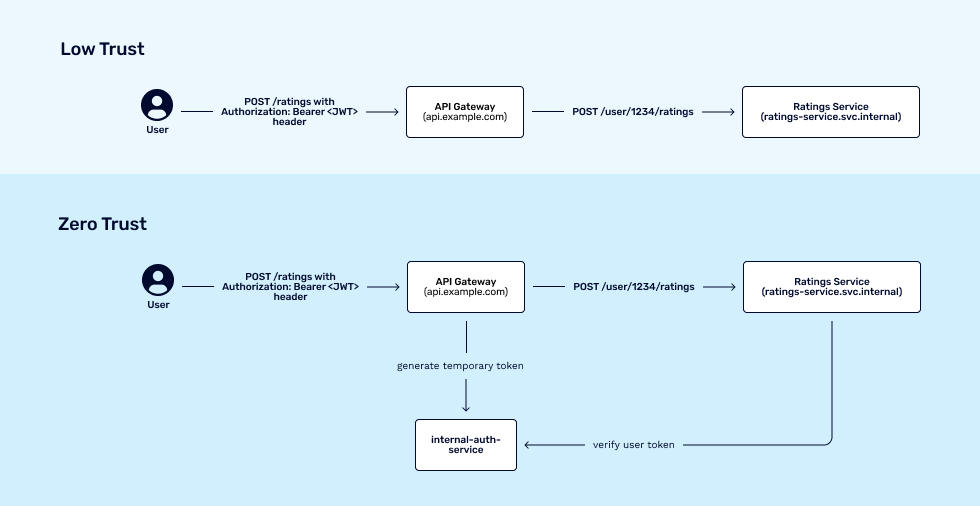
![SYSTEM DESIGN] authentication microservice for multiple backend microservices - Blind SYSTEM DESIGN] authentication microservice for multiple backend microservices - Blind](https://d2u3dcdbebyaiu.cloudfront.net/uploads/atch_img/60/5df5da438697b629d7a3330f61fe45f1_res.png)